There and Back Again a Packets
How Does the Cyberspace Work?
� 2002 Rus Shuler @ Pomeroy IT Solutions, all rights reservedContents
- Introduction
- Where to Begin? Internet Addresses
- Protocol Stacks and Packets
- Networking Infrastructure
- Internet Infrastructure
- The Net Routing Bureaucracy
- Domain Names and Address Resolution
- Internet Protocols Revisited
- Application Protocols: HTTP and the Globe Broad Spider web
- Awarding Protocols: SMTP and Electronic mail
- Transmission Command Protocol
- Internet Protocol
- Wrap Up
- Resources
- Bibliography
Introduction
How does the Net work? Good question! The Internet's growth has become explosive and it seems impossible to escape the battery of world wide web.com'due south seen constantly on television set, heard on radio, and seen in magazines. Because the Cyberspace has get such a large role of our lives, a adept agreement is needed to use this new tool almost effectively.This whitepaper explains the underlying infrastructure and technologies that brand the Internet piece of work. Information technology does not get into great depth, but covers enough of each area to give a bones understanding of the concepts involved. For any unanswered questions, a list of resources is provided at the end of the newspaper. Whatsoever comments, suggestions, questions, etc. are encouraged and may be directed to the author at rshuler@gobcg.com.
Where to Begin? Internet Addresses
Because the Internet is a global network of computers each computer connected to the Internet must take a unique address. Net addresses are in the form nnn.nnn.nnn.nnn where nnn must be a number from 0 - 255. This address is known as an IP accost. (IP stands for Internet Protocol; more on this later.)The motion picture below illustrates ii computers connected to the Internet; your computer with IP address i.2.three.4 and another computer with IP address 5.six.vii.8. The Net is represented equally an abstract object in-between. (As this paper progresses, the Internet portion of Diagram 1 will be explained and redrawn several times as the details of the Internet are exposed.)
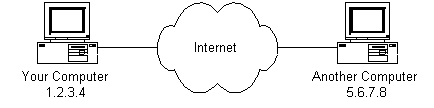 |
| Diagram 1 |
| Bank check It Out - The Ping Plan |
| If you're using Microsoft Windows or a flavor of Unix and have a connection to the Net, there is a handy program to come across if a estimator on the Net is alive. It'due south chosen ping, probably after the audio made by older submarine sonar systems.one If you are using Windows, first a command prompt window. If you're using a flavor of Unix, become to a command prompt. Type ping world wide web.yahoo.com. The ping plan will transport a 'ping' (actually an ICMP (Internet Control Message Protocol) repeat request message) to the named estimator. The pinged figurer will respond with a answer. The ping program volition count the fourth dimension expired until the reply comes dorsum (if it does). Also, if you enter a domain proper name (i.e. www.yahoo.com) instead of an IP address, ping will resolve the domain name and display the computer's IP address. More on domain names and address resolution later. |
Protocol Stacks and Packets
Then your estimator is continued to the Cyberspace and has a unique accost. How does information technology 'talk' to other computers connected to the Internet? An instance should serve here: Let's say your IP address is one.2.iii.4 and you want to send a message to the figurer 5.6.7.8. The message you desire to send is "Hello estimator five.6.vii.8!". Obviously, the bulletin must be transmitted over whatever kind of wire connects your computer to the Cyberspace. Let'south say you've dialed into your Isp from home and the message must exist transmitted over the telephone line. Therefore the message must be translated from alphabetic text into electronic signals, transmitted over the Internet, so translated back into alphabetic text. How is this accomplished? Through the apply of a protocol stack. Every computer needs one to communicate on the Internet and information technology is usually built into the computer'due south operating organization (i.e. Windows, Unix, etc.). The protocol stack used on the Internet is refered to as the TCP/IP protocol stack because of the 2 major communication protocols used. The TCP/IP stack looks like this:| Protocol Layer | Comments |
|---|---|
| Application Protocols Layer | Protocols specific to applications such equally Www, e-mail, FTP, etc. |
| Transmission Control Protocol Layer | TCP directs packets to a specific application on a figurer using a port number. |
| Internet Protocol Layer | IP directs packets to a specific computer using an IP address. |
| Hardware Layer | Converts binary packet data to network signals and back. (E.1000. ethernet network card, modem for phone lines, etc.) |
If nosotros were to follow the path that the message "How-do-you-do figurer v.six.7.8!" took from our reckoner to the calculator with IP address 5.6.7.8, information technology would happen something similar this:
 |
| Diagram 2 |
- The message would starting time at the top of the protocol stack on your computer and work it's mode downwardly.
- If the message to be sent is long, each stack layer that the message passes through may pause the message up into smaller chunks of data. This is because information sent over the Internet (and most calculator networks) are sent in manageable chunks. On the Internet, these chunks of data are known every bit packets.
- The packets would go through the Application Layer and go on to the TCP layer. Each packet is assigned a port number. Ports will be explained later, merely suffice to say that many programs may be using the TCP/IP stack and sending letters. We demand to know which programme on the destination reckoner needs to receive the message considering it will be listening on a specific port.
- Afterward going through the TCP layer, the packets keep to the IP layer. This is where each package receives information technology's destination address, 5.6.vii.8.
- At present that our message packets accept a port number and an IP address, they are ready to be sent over the Net. The hardware layer takes care of turning our packets containing the alphabetic text of our message into electronic signals and transmitting them over the telephone line.
- On the other end of the phone line your Isp has a directly connection to the Internet. The ISPs router examines the destination address in each packet and determines where to send it. Often, the bundle'southward side by side end is some other router. More on routers and Cyberspace infrastructure later on.
- Somewhen, the packets reach estimator 5.half dozen.7.8. Here, the packets offset at the bottom of the destination calculator's TCP/IP stack and work up.
- Equally the packets get upwardly through the stack, all routing data that the sending figurer's stack added (such as IP accost and port number) is stripped from the packets.
- When the information reaches the top of the stack, the packets have been re-assembled into their original form, "Hullo reckoner 5.vi.seven.eight!"
Networking Infrastructure
So at present y'all know how packets travel from one computer to another over the Internet. Merely what's in-between? What actually makes up the Internet? Let'south await at another diagram: 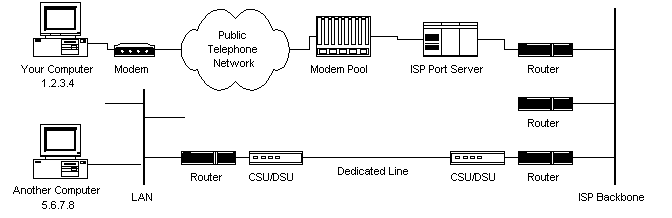 |
| Diagram 3 |
The ISP maintains a pool of modems for their dial-in customers. This is managed by some course of figurer (usually a defended i) which controls information flow from the modem pool to a courage or dedicated line router. This setup may be refered to as a port server, every bit information technology 'serves' access to the network. Billing and usage data is usually collected here likewise.
Afterwards your packets traverse the telephone network and your Internet access provider'southward local equipment, they are routed onto the ISP's courage or a backbone the Internet access provider buys bandwidth from. From here the packets will usually journey through several routers and over several backbones, dedicated lines, and other networks until they observe their destination, the computer with accost 5.6.7.8. But wouldn't it would exist nice if nosotros knew the exact route our packets were taking over the Internet? As it turns out, there is a way...
| Check Information technology Out - The Traceroute Program |
| If you're using Microsoft Windows or a flavor of Unix and have a connection to the Net, here is some other handy Internet program. This one is chosen traceroute and information technology shows the path your packets are taking to a given Cyberspace destination. Like ping, you lot must employ traceroute from a control prompt. In Windows, apply tracert www.yahoo.com. From a Unix prompt, type traceroute www.yahoo.com. Like ping, y'all may also enter IP addresses instead of domain names. Traceroute will print out a listing of all the routers, computers, and whatsoever other Cyberspace entities that your packets must travel through to get to their destination. |
If you utilise traceroute, you'll discover that your packets must travel through many things to go to their destination. Most have long names such as sjc2-core1-h2-0-0.atlas.digex.net and fddi0-0.br4.SJC.globalcenter.net. These are Internet routers that make up one's mind where to send your packets. Several routers are shown in Diagram three, simply only a few. Diagram 3 is meant to prove a uncomplicated network structure. The Internet is much more complex.
Internet Infrastructure
The Net backbone is fabricated up of many large networks which interconnect with each other. These large networks are known every bit Network Service Providers or NSPdue south. Some of the large NSPs are UUNet, CerfNet, IBM, BBN Planet, SprintNet, PSINet, besides as others. These networks peer with each other to exchange packet traffic. Each NSP is required to connect to three Network Access Points or NAPs. At the NAPs, packet traffic may jump from one NSP'due south backbone to some other NSP's backbone. NSPs also interconnect at Metropolitan Area Exchanges or MAEs. MAEs serve the same purpose as the NAPs but are privately owned. NAPs were the original Internet interconnect points. Both NAPs and MAEs are referred to as Cyberspace Exchange Points or Ninesouth. NSPs also sell bandwidth to smaller networks, such every bit ISPs and smaller bandwidth providers. Below is a picture showing this hierarchical infrastructure. 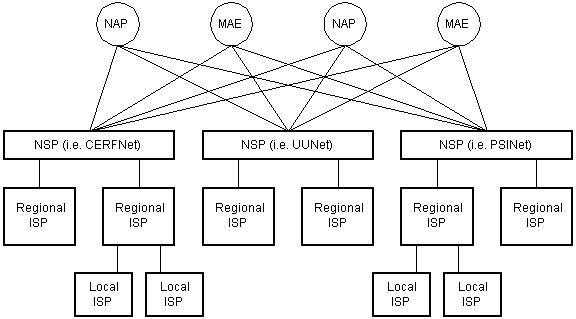 |
| Diagram 4 |
The Internet Routing Hierarchy
So how do packets find their style across the Net? Does every calculator connected to the Internet know where the other computers are? Do packets simply get 'broadcast' to every figurer on the Internet? The answer to both the preceeding questions is 'no'. No reckoner knows where whatever of the other computers are, and packets do non go sent to every reckoner. The information used to get packets to their destinations are independent in routing tables kept past each router connected to the Internet.Routers are packet switches. A router is usually connected between networks to road packets between them. Each router knows most it's sub-networks and which IP addresses they use. The router normally doesn't know what IP addresses are 'above' it. Examine Diagram v below. The black boxes connecting the backbones are routers. The larger NSP backbones at the meridian are connected at a NAP. Under them are several sub-networks, and under them, more sub-networks. At the bottom are two local area networks with computers fastened.
 |
| Diagram 5 |
Domain Names and Address Resolution
Just what if you don't know the IP address of the computer you want to connect to? What if the you demand to admission a spider web server referred to as www.anothercomputer.com? How does your spider web browser know where on the Internet this figurer lives? The reply to all these questions is the Domain Name Service or DNS. The DNS is a distributed database which keeps rail of calculator'due south names and their corresponding IP addresses on the Cyberspace.Many computers connected to the Internet host function of the DNS database and the software that allows others to admission it. These computers are known as DNS servers. No DNS server contains the entire database; they just contain a subset of information technology. If a DNS server does not incorporate the domain name requested by another computer, the DNS server re-directs the requesting computer to another DNS server.
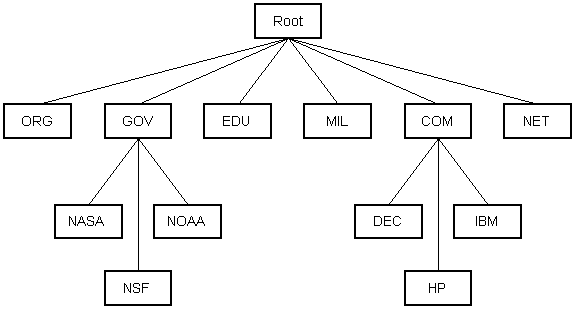 |
| Diagram half dozen |
When an Net connexion is setup (e.thou. for a LAN or Punch-Upward Networking in Windows), one primary and i or more than secondary DNS servers are usually specified equally part of the installation. This manner, any Cyberspace applications that need domain name resolution volition exist able to function correctly. For example, when you enter a web address into your spider web browser, the browser first connects to your primary DNS server. After obtaining the IP address for the domain name you entered, the browser then connects to the target computer and requests the spider web page you wanted.
| Check It Out - Disable DNS in Windows |
| If yous're using Windows 95/NT and access the Internet, you may view your DNS server(southward) and even disable them. If you use Punch-Up Networking: If you have a permanent connection to the Internet: You should now be looking at your DNS servers' IP addresses. Hither you may disable DNS or gear up your DNS servers to 0.0.0.0. (Write down your DNS servers' IP addresses first. You lot volition probably accept to restart Windows likewise.) At present enter an accost into your spider web browser. The browser won't be able to resolve the domain name and yous will probably get a nasty dialog box explaining that a DNS server couldn't be found. Even so, if you enter the corresponding IP address instead of the domain name, the browser will be able to call up the desired web page. (Use ping to go the IP address prior to disabling DNS.) Other Microsoft operating systems are similar. |
Internet Protocols Revisited
As hinted to before in the section about protocol stacks, one may surmise that there are many protocols that are used on the Net. This is truthful; in that location are many communication protocols required for the Internet to role. These include the TCP and IP protocols, routing protocols, medium admission control protocols, application level protocols, etc. The following sections describe some of the more important and commonly used protocols on the Net. College level protocols are discussed offset, followed by lower level protocols.Awarding Protocols: HTTP and the World Wide Spider web
One of the about usually used services on the Cyberspace is the World Wide Spider web (WWW). The application protocol that makes the web piece of work is Hypertext Transfer Protocol or HTTP. Do not misfile this with the Hypertext Markup Linguistic communication (HTML). HTML is the language used to write web pages. HTTP is the protocol that web browsers and web servers use to communicate with each other over the Internet. Information technology is an awarding level protocol because it sits on top of the TCP layer in the protocol stack and is used by specific applications to talk to one another. In this case the applications are spider web browsers and web servers.HTTP is a connectionless text based protocol. Clients (web browsers) send requests to spider web servers for web elements such as spider web pages and images. After the asking is serviced past a server, the connection betwixt customer and server across the Internet is disconnected. A new connexion must be made for each asking. Nigh protocols are connection oriented. This means that the two computers communicating with each other keep the connection open up over the Cyberspace. HTTP does not yet. Before an HTTP asking can be made by a client, a new connection must exist made to the server.
When you blazon a URL into a web browser, this is what happens:
- If the URL contains a domain proper name, the browser first connects to a domain proper name server and retrieves the corresponding IP accost for the spider web server.
- The web browser connects to the web server and sends an HTTP request (via the protocol stack) for the desired web page.
- The web server receives the request and checks for the desired page. If the page exists, the web server sends information technology. If the server cannot find the requested folio, it will send an HTTP 404 mistake message. (404 means 'Folio Not Plant' as anyone who has surfed the web probably knows.)
- The web browser receives the page back and the connectedness is closed.
- The browser and then parses through the page and looks for other page elements information technology needs to complete the spider web page. These usually include images, applets, etc.
- For each chemical element needed, the browser makes additional connections and HTTP requests to the server for each element.
- When the browser has finished loading all images, applets, etc. the page will be completely loaded in the browser window.
| Check Information technology Out - Use Your Telnet Client to Retrieve a Web Folio Using HTTP |
| Telnet is a remote terminal service used on the Internet. Information technology's utilise has declined lately, but it is a very useful tool to study the Cyberspace. In Windows find the default telnet program. Information technology may be located in the Windows directory named telnet.exe. When opened, pull down the Concluding menu and select Preferences. In the preferences window, check Local Repeat. (This is so you can see your HTTP request when you type it.) Now pull downwards the Connection card and select Remote Organisation. Enter www.google.com for the Host Proper name and 80 for the Port. (Web servers normally listen on port 80 by default.) Press Connect. Now blazon Become / HTTP/1.0 and press Enter twice. This is a uncomplicated HTTP asking to a spider web server for it'southward root page. You lot should run across a web page wink past and then a dialog box should pop up to tell you the connection was lost. If you'd similar to save the retrieved page, turn on logging in the Telnet programme. You may and so browse through the web page and see the HTML that was used to write information technology. |
Most Internet protocols are specified by Cyberspace documents known equally a Request For Comments or RFCs. RFCs may be constitute at several locations on the Cyberspace. See the Resources section below for appropriate URL's. HTTP version 1.0 is specified by RFC 1945.
Application Protocols: SMTP and Electronic Post
Another commonly used Cyberspace service is electronic mail. Electronic mail uses an application level protocol called Simple Mail Transfer Protocol or SMTP. SMTP is also a text based protocol, but unlike HTTP, SMTP is connection oriented. SMTP is also more complicated than HTTP. There are many more commands and considerations in SMTP than in that location are in HTTP.When you open up your mail customer to read your e-mail, this is what typically happens:
- The postal service client (Netscape Mail, Lotus Notes, Microsoft Outlook, etc.) opens a connectedness to it'south default mail service server. The mail service server'southward IP address or domain name is typically setup when the mail client is installed.
- The mail server will always transmit the first message to place itself.
- The client volition send an SMTP HELO control to which the server volition respond with a 250 OK bulletin.
- Depending on whether the customer is checking mail, sending mail service, etc. the appropriate SMTP commands will be sent to the server, which will respond appropriately.
- This asking/response transaction will continue until the client sends an SMTP QUIT command. The server will then say goodbye and the connection volition be closed.
This SMTP example shows mail service sent past Smith at host USC-ISIF, to Jones, Green, and Brown at host BBN-UNIX. Here nosotros presume that host USC-ISIF contacts host BBN-UNIX directly. The postal service is accepted for Jones and Brown. Green does not have a mailbox at host BBN-UNIX. ------------------------------------------------------------- R: 220 BBN-UNIX.ARPA Elementary Mail Transfer Service Prepare S: HELO USC-ISIF.ARPA R: 250 BBN-UNIX.ARPA S: Postal service FROM:<Smith@USC-ISIF.ARPA> R: 250 OK South: RCPT TO:<Jones@BBN-UNIX.ARPA> R: 250 OK South: RCPT TO:<Green@BBN-UNIX.ARPA> R: 550 No such user here Due south: RCPT TO:<Brownish@BBN-UNIX.ARPA> R: 250 OK S: Information R: 354 Commencement postal service input; stop with <CRLF>.<CRLF> S: Blah blah apathetic... S: ...etc. etc. etc. S: . R: 250 OK S: QUIT R: 221 BBN-UNIX.ARPA Service endmost transmission aqueductThis SMTP transaction is taken from RFC 821, which specifies SMTP.
Transmission Control Protocol
Under the application layer in the protocol stack is the TCP layer. When applications open a connection to another figurer on the Net, the letters they send (using a specific application layer protocol) get passed downwardly the stack to the TCP layer. TCP is responsible for routing application protocols to the correct application on the destination reckoner. To accomplish this, port numbers are used. Ports can exist thought of equally seperate channels on each computer. For case, you lot can surf the web while reading electronic mail. This is because these two applications (the web browser and the mail client) used different port numbers. When a packet arrives at a calculator and makes its manner up the protocol stack, the TCP layer decides which application receives the package based on a port number.TCP works similar this:
- When the TCP layer receives the application layer protocol data from in a higher place, it segments it into manageable 'chunks' and then adds a TCP header with specific TCP information to each 'chunk'. The data independent in the TCP header includes the port number of the application the information needs to exist sent to.
- When the TCP layer receives a packet from the IP layer below information technology, the TCP layer strips the TCP header data from the bundle, does some information reconstruction if necessary, then sends the data to the right application using the port number taken from the TCP header.
TCP is non a textual protocol. TCP is a connectedness-oriented, reliable, byte stream service. Connexion-oriented means that two applications using TCP must showtime institute a connection before exchanging information. TCP is reliable because for each packet received, an acknowledgement is sent to the sender to confirm the commitment. TCP also includes a checksum in it's header for error-checking the received data. The TCP header looks like this:
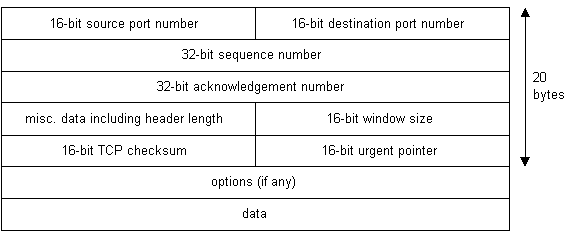 |
| Diagram vii |
| Cheque Information technology Out - Well Known Internet Port Numbers | ||||||||||
Listed below are the port numbers for some of the more commonly used Cyberspace services.
|
Cyberspace Protocol
Unlike TCP, IP is an unreliable, connectionless protocol. IP doesn't care whether a packet gets to information technology'due south destination or not. Nor does IP know about connections and port numbers. IP's job is too send and route packets to other computers. IP packets are independent entities and may arrive out of society or not at all. It is TCP's job to make sure packets arrive and are in the right order. About the merely matter IP has in common with TCP is the style it receives data and adds it's own IP header data to the TCP data. The IP header looks like this: 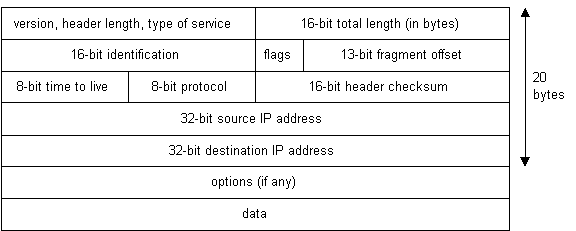 |
| Diagram eight |
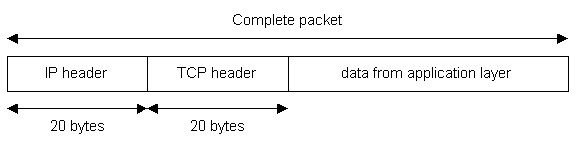 |
| Diagram 9 |
Wrap Up
Now you know how the Internet works. Only how long will it stay this fashion? The version of IP currently used on the Net (version iv) only allows 232 addresses. Eventually there won't exist whatever free IP addresses left. Surprised? Don't worry. IP version 6 is being tested right at present on a enquiry backbone by a consortium of inquiry institutions and corporations. And afterward that? Who knows. The Cyberspace has come a long manner since it'southward inception as a Defense Department enquiry project. No one really knows what the Internet volition become. One thing is certain, however. The Internet will unite the world like no other mechanism e'er has. The Information Age is in full stride and I am glad to be a part of information technology.Rus Shuler, 1998
Updates made 2002
Resources
Below are some interesting links associated with some of the topics discussed. (I hope they all still work. All open in new window.)http://world wide web.ietf.org/ is the home page of the Net Engineering Task Force. This body is greatly responsible for the development of Internet protocols and the like.
http://www.internic.org/ is the organization responsible for administering domain names.
http://www.nexor.com/public/rfc/index/rfc.html is an excellent RFC search engine useful for finding any RFC.
http://world wide web.internetweather.com/ shows animated maps of Cyberspace latency.
http://routes.clubnet.cyberspace/iw/ is Internet Conditions from ClubNET. This folio shows packet loss for various carriers.
http://navigators.com/isp.html is Russ Haynal'south Internet access provider Page. This is a great site with links to most NSPs and their backbone infrastructure maps.
Bibliography
The following books are excellent resources and helped profoundly in the writing of this paper. I believe Stevens' book is the all-time TCP/IP reference ever and can be considered the bible of the Cyberspace. Sheldon's volume covers a much wider scope and contains a vast amount of networking information.- TCP/IP Illustrated, Volume 1, The Protocols.
West. Richard Stevens.
Addison-Wesley, Reading, Massachusetts. 1994. - Encyclopedia of Networking.
Tom Sheldon.
Osbourne McGraw-Hill, New York. 1998.
- Firewalls and Internet Security; Repelling the Wiley Hacker.
William R. Cheswick, Steven M. Bellovin.
Addison-Wesley, Reading, Massachusetts. 1994. - Data Communications, Calculator Networks and Open Systems. Fourth Edition.
Fred Halsall.
Addison-Wesley, Harlow, England. 1996. - Telecommunications: Protocols and Blueprint.
John D. Spragins with Joseph L. Hammond and Krzysztof Pawlikowski.
Addison-Wesley, Reading, Massachusetts. 1992.
Source: https://web.stanford.edu/class/msande91si/www-spr04/readings/week1/InternetWhitepaper.htm
0 Response to "There and Back Again a Packets"
Enregistrer un commentaire